IT Empowerment Blog
Episode 1: Miles Veth
Nicholas Paulukow talks with Miles Veth of the Veth Group, about his marketing company and how Christianity has influenced business practices.
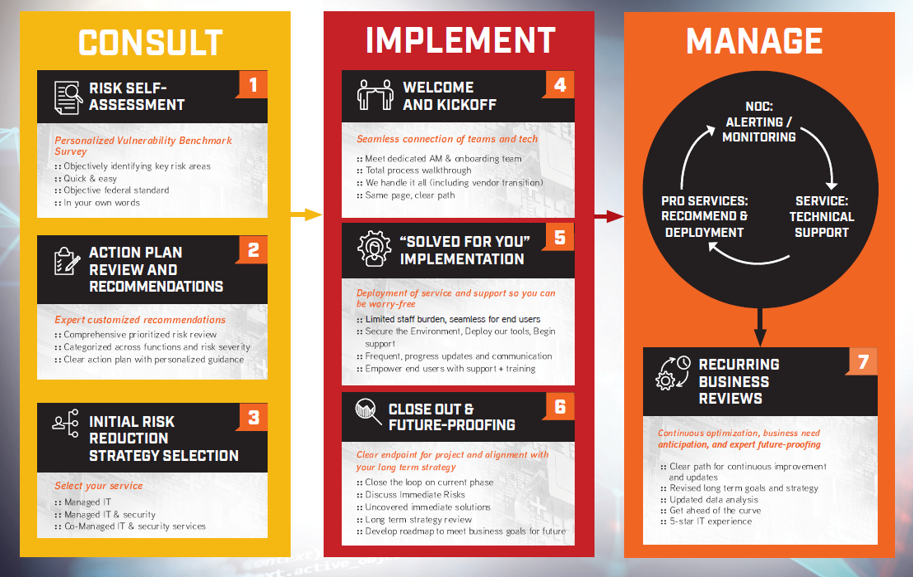
How Long Does IT Onboarding Take?
IT onboarding with ONE 2 ONE will strengthen your IT with our consult, implement, and manage phases for a tailored 5-star experience.
It’s Time for Extra Give, Lancaster!
Lancaster’s Extra Give 2023 begins on November 17th. Learn more about the program, plus support the clients we work with every day!
IoT Security Challenges: Mitigating Risks in an Ever-Connected Age
Explore the rise of the Internet of Things and how to plug the cybersecurity gaps associated with IoT devices.
APIs and Cybersecurity: Securing the Digital Frontier
Explore the critical role of APIs and cybersecurity. Learn their vulnerabilities, the risks they pose, and practices to protect your business.
How the Cost of a Data Breach Affects Your Bottom Line
Exploring the cost of a data breach at $4.5M Globally and $9.4M in the U.S. Safeguard your bottom line now!
A Comprehensive Guide to Combatting Insider Threats: IT Security’s Growing Dilemma
Unlock the Guide to Battling Insider Threats! Safeguard your company’s finances and reputation from risks within your own walls.
The Role of IT Support in Cybersecurity: A Guide for CFOs
Learn the key role of IT support in cybersecurity. Discover how you can strategize for digital asset protection and long-term growth.
Endpoint Detection and Response: Why your antivirus isn’t enough!
Endpoint Detection and Response solutions have increasingly been adopted by companies around the U.S. Learn why here!
Where Do Cyberattacks Start, and Are Your Ready for One?
Can you really be ready for a cyberattack? Yes, you can! Learn where cyberattacks come from, the malware hackers use, and how to be ready!
Employee Security Training: We do it too!
Employee security training should be a part of your cybersecurity plan. It’s so important that we do it too.
How to Plan and Develop a Cybersecurity Strategy
Your company needs a cybersecurity strategy. If you don’t have one in place, you’re putting data at risk. Use these 8 steps to get started!