A SIEM Solution, by any other name
A sweet-smelling breakdown of ONE 2 ONE’s log aggregation and other SIEM software features
Benefits of Modern SIEM Tools
Centralize your SIEM, skip the giant price tag
ONE 2 ONE is a Co-Managed Threat Detection and Response Platform. ONE 2 ONE detects, while our Security Operations Center (SOC) responds. You have full access to view your security data, and can even have your security teams analyze alongside us.
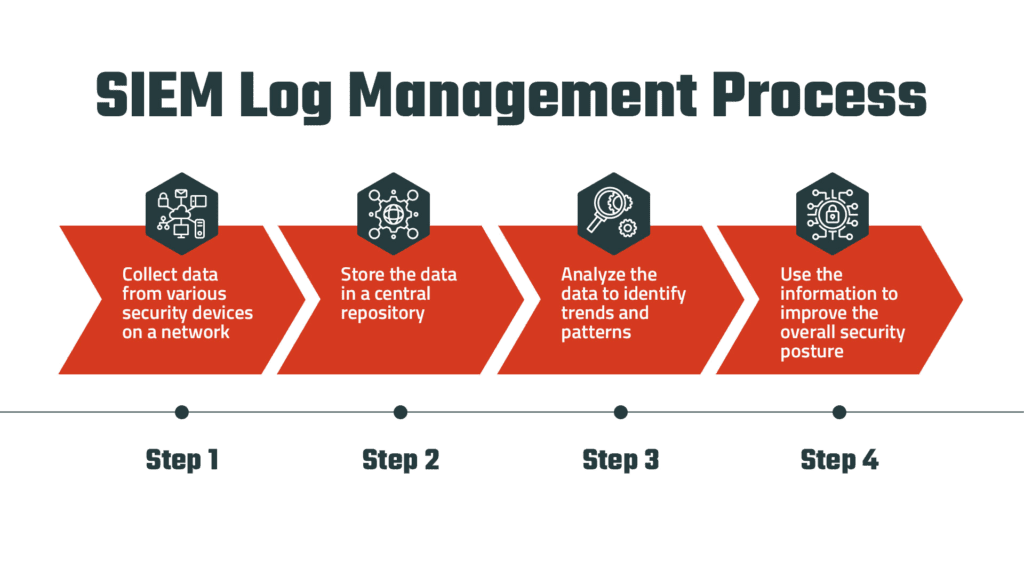
We baked our customers’ most-requested SIEM solution right into the ONE 2 ONE SIEM platform. Now you can access these features directly within the ONE 2 ONE SIEM systems:

Enhance ONE 2 ONE’s analysis of your IT infrastructure
Whether you prefer to call it SIEM, data lake, or log aggregation, adding security information management enhances your view of your security analytics. ONE 2 ONE SOC is now detecting and investigating cyberattacks within log metadata. You and your clients can store logs for compliance without any other tools. If you’re considering a modern SIEM solution with those goals in mind, ONE 2 ONE maybe the right option for you.
ONE 2 ONE’s Next-Gen SIEM
Feature |
BENEFIT |
||
COLLECT |
Windows event logs | Insight into services activity and changes, including Active Directory | |
| Syslog data | Insight into endpoint activity, including firewall logs, change management tracking and error logs | ||
| Event parsing | Supports strong auditing, search and reporting | ||
| Collected alongside network data sources | View log data next to the critical network data you’re already collecting to further enrich the picture around potential security threats | ||
| Flexible retention | Keep your data for as long as you want – meet your regulatory retention requirements easily |
||
| Easy deployment | If your ONE 2 ONE sensor is already in your environment, just point your logs our way for collection and retention |
||
DETECT |
Activity detection | Extended threat detection rules for dozens of vendors ensure the broadest out-of-the-box overage possible | |
| Event correlation | ONE 2 ONE SOC includes collected log data in their analysis to correlate events and further identify cyber threats | ||
| Security alerts | ONE 2 ONE alerts on bad network activity and escalates to you after our SOC has investigated the incident. SOC uses log data to enrich the context of the network activity to provide even more fidelity when investigating advanced threats | ||
RESPOND |
Dashboards | Understand log (and network) activity in a glance with a fully customizable view | |
| Reports | Gain insight into the data you’re seeing and ensure organizational and compliance reporting by generating reports around sensitive data patterns | ||
| Searching and threat hunting |
Conduct forensic investigations – access network data and O365 log history in a single pane of glass via ONE 2 ONEybana |
Office 365® SIEM Tools
STAND-ALONE LOG AGGREGATION
(INCLUDED WITH ONE 2 ONE SIEM)
SIEM Solution Capabilities
Include your Office 365 logs in ONE 2 ONE’s threat detection
Empower ONE 2 ONE’s Security Operations Center (SOC) to defend your business from account takeovers and business email compromise (BEC) and satisfy compliance requirements. With O365 integration, ONE 2 ONE generates alerts through the ONE 2 ONE platform based on your Office 365 logs. From your ONE 2 ONE console, you can customize which alerts you receive and how you receive them. Then investigate any impact through Perchybana in real time; or let our SOC automation do it for you.


Security Event Monitoring Service
With Office 365 integration, ONE 2 ONE provides everything you need for incident response and investigate alerts from Office 365 logs. With ONE 2 ONE, logs are searchable, parsed, cleaned, and reportable. And you can increase log retention without the extra price tag to satisfy compliance requirements.
Take advantage of ONE 2 ONE’s comprehensive list of pre-configured notification alerts to defend yourself from malicious activity, including:
ONE 2 ONE gives you the SIEM solutions to decipher the magnitude of an incident and pinpoint what exactly is affected.
ONE 2 ONE’s Office 365 Functionality
Feature |
BENEFIT |
||
COLLECT & CUSTOMIZE |
Authentication logs | Insight into authentication attempts against your Office 365 tenant | |
| File access and change logs | Insight into SharePoint and OneDrive activity, including access, changes, and deletion of files | ||
| Event parsing | Supports strong auditing, search and reporting | ||
| Collected alongside network data sources | View log data next to the critical network data you’re already collecting to further enrich the picture around potential incidents | ||
| Flexible retention | Keep your data for as long as you want – meet your regulatory retention requirements easily |
||
| Easy deployment | Single-click deployment of Office 365 logging in the ONE 2 ONE environment; no hardware or onsite installation required to collect the required logs | ||
DETECT |
Activity detection | Pre-built detection rules for the highest risk activities | |
| Event correlation | ONE 2 ONE SOC includes collected log data in their analysis to correlate events and further identify potential security threats | ||
| Security alerts | ONE 2 ONE security tools alert on malicious and high-risk activities and escalates to you after our SOC has investigated the incident. ONE 2 ONE SOC uses log data to enrich the context of the network activity to provide even more fidelity when investigating potential threats | ||
RESPOND |
Dashboards | Understand log (and network) activity in a glance with a fully customizable view | |
| Reports | Gain insight into the data you’re seeing and ensure organizational and regulatory compliance by generating reports around interesting data patterns | ||
| Searching and threat hunting |
Conduct forensic investigations – access network data and O365 log history in a single pane of glass via ONE 2 ONEybana |
SIEM Solution, a recap on security event management
Security Monitoring
A SIEM solution can access multiple data sources, including traditional antivirus (AV) and authentication logs, allowing security teams to identify security incidents beyond what an individual security tool can catch.
Advanced Threat Detection
SIEM solutions detect, mitigate, and prevent advanced threats like malicious insider threats, data exfiltration, and outsider threats.
Fast Incident Response
Collecting data to understand a security incident after it happens takes time. SIEM automatically collects this data and reduces response time. SIEM will provide forensic data to uncover the kill chain, threat actors, and mitigation.
Compliance Reporting and Auditing
Modern SIEM solutions automatically provide monitoring and reporting to meet HIPAA, PCI DSS, SOX, FERPA, and HITECH standards.
See us in action!
Explore our success stories to see how companies like yours have benefited from
our managed IT services and expertise.
