AzureAD and MFA
Guidelines
Microsoft AzureAD / Hello for Business /
MFA Best Practices
MFA Supplies Added Security
AzureAD Multi-Factor Authentication (MFA) supplies added security for your identities by requiring two or more elements for full authentication.
These elements fall into three categories:

AzureAD and Hello For Business Authentication:
Implementing AzureAD and Windows HELLO for Business provides stronger multi-factor authentication. Hello for Business is specific to your device authentication, not for your Microsoft 365 account. The Windows Hello for Business key meets AzureAD multi-factor authentication (MFA) requirements and reduces the number of MFA prompts users will see when accessing resources.
To utilize the Multi-Factor Unlock feature of Hello for Business, you have these options available – you must pick one from each list and they cannot be duplicated: (PIN + PIN does not work)
First Unlock Factor:
Important: To utilize Facial Recognition the camera must support Hello for Business, and to Utilize Fingerprint, a Windows Hello for Business compatible fingerprint reader is required. Some built-ins are supported.
Second Unlock Factor:
Important: To utilize Bluetooth Paired Smartphone, a smartphone with Bluetooth is required. Also, the device they are logging into must support Bluetooth (Most laptops, not most workstations. A Bluetooth add on USB for a device without built-in is an option.
Microsoft 365 Authenticator App for Cloud-Based Authentication:
The Microsoft 365 Authenticator app provides an additional level of security to your AzureAD work or school account or your Microsoft account and is available for Android and iOS. With the Microsoft 365 Authenticator app, users can authenticate in a passwordless way during sign-in, or as an additional verification option during self-service password reset (SSPR), or AzureAD Multi-Factor Authentication events.
For more granular controls, Conditional Access policies can be used to define events or applications that require MFA. These policies can allow regular sign-in events when the user is on the corporate network or a registered device, but prompt for additional verification factors when remote or on a personal device.
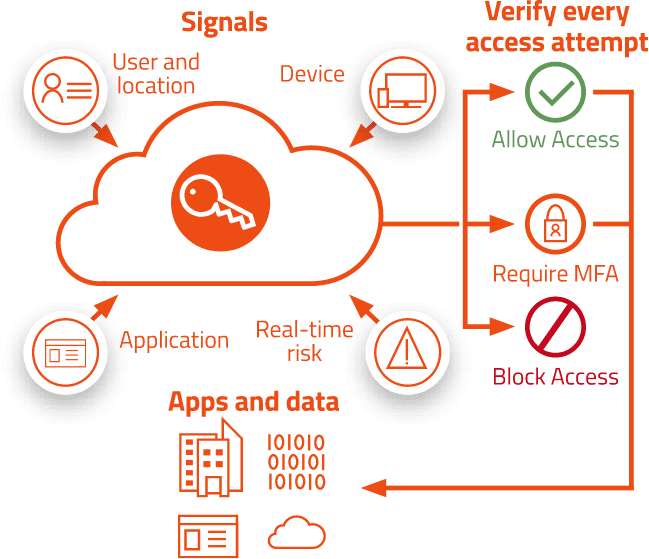
Instead of seeing a prompt for a password after entering a username, a user that has enabled phone sign-in from the Microsoft 365 Authenticator app sees a message to enter a number in their app. When the correct number is selected, the sign-in process is complete. The Authenticator app can help prevent unauthorized access to accounts and stop fraudulent transactions by pushing a notification to your smartphone or tablet. Users view the notification, and if it’s legitimate, select Verify. Otherwise, they can select Deny.

Recommended signals
Common decisions


Recommended Policies
See us in action!
Explore our success stories to see how companies like yours have benefited from
our managed IT services and expertise.
