
Zero Trust for SMBs: Why It Matters and How to Start (Webinar Recap)
Video Replay Included
Cyber threats are evolving faster than most small and mid-sized businesses can keep pace with, and attackers are aware of this. With automation, AI, and credential dumps readily available on the dark web, SMBs have become the easiest and most profitable targets. That’s exactly why Zero Trust Security for Small Businesses has shifted from an enterprise concept to an essential strategy for organizations of every size.
This post breaks down the core lessons from our webinar on Zero Trust, walking you through what it is, why it matters, and how to begin implementing it in your business.
Watch the full webinar replay
Why SMBs Are Now Prime Targets
Not long ago, cybercriminals focused heavily on large enterprises. But today, the trend has completely flipped. Research shows that 82% of ransomware attacks now target SMBs.
Why the shift?
- SMBs often lack the layered defenses enterprises use
- Employees may reuse passwords or fall for phishing
- Cloud platforms are often misconfigured or unmonitored
- Attackers can automate massive attacks with AI
Reports from Verizon and the FBI reinforce three primary causes of modern breaches:
- Compromised credentials
- Phishing and social engineering
- Exploited vulnerabilities
These categories account for the overwhelming majority of successful attacks.
And with exploited vulnerabilities up 180% year-over-year, even one unpatched system can become an entry point. This is exactly why conversations around Zero Trust Security for Small Businesses are becoming more urgent.
Business Email Compromise: The Most Expensive Threat
One threat stands above the rest in terms of financial damage: Business Email Compromise (BEC).
According to the FBI:
- BEC causes nearly $3 billion in losses yearly
- The median loss is around $50,000
- For many SMBs, that’s devastating
As AI improves, emails look increasingly real. These scams often involve:
- Fake payment requests
- Vendor impersonation
- Manipulated invoices
- Fraudulent wiring details
Zero Trust principles, which verify, authenticate, and validate behavior, are foundational protections against BEC.
Zero Trust: A Framework, Not a Product
A common misconception is that Zero Trust is a tool you can buy.
It isn’t.
It’s a security framework built on three principles:
- Never trust by default
- Always verify
- Enforce least privilege
Zero Trust assumes every request, inside or outside your network, could be compromised. Access is granted only after identity, device, and context have all been validated. This mindset is the backbone of Zero Trust Security for Small Businesses, ensuring that even if one control fails, others stand ready.
Context-Aware Access: Why Location Matters
Traditional security verifies a username and password. Zero Trust goes further by asking:
- Is this login from a typical location?
- Is this device recognized?
- Is this behavior normal?
If you normally log in from Tampa and there’s a login attempt from London minutes later, Zero Trust systems trigger additional verification or block the attempt entirely.
This type of context-aware access is an easy win in any Zero Trust Security for Small Businesses strategy.
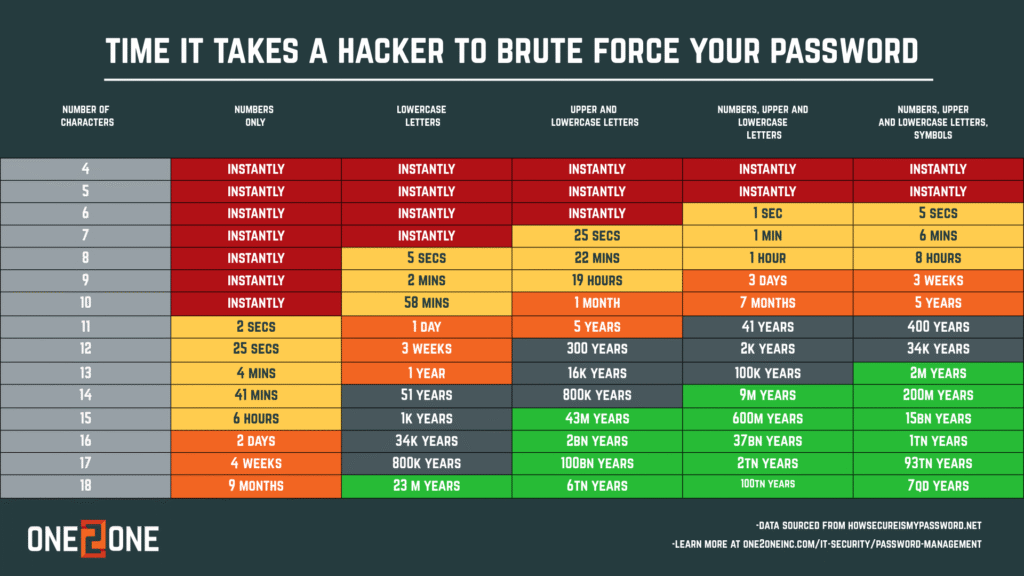
Passwords Are No Longer Enough
Even complex 8-character passwords can be cracked in about five minutes.
But the bigger issue? Password reuse.
Many employees recycle personal passwords at work or slightly modify old ones. Once those personal accounts are breached, attackers use automated tools to test the same credentials across business platforms.
Strong, unique, long passwords and a password manager to help manage them are essential Zero Trust building blocks.
MFA: Strong vs. Weak Methods
Multi-factor authentication (MFA) dramatically reduces account takeover risk, but only if you choose strong methods.
Strongest MFA Options:
- Hardware keys (e.g., YubiKeys)
- Passkeys tied to your device
- Secure biometrics
Nearly impossible to phish.
Moderately Strong:
- App-based authentication with unique codes
Weakest:
- SMS or voice-based codes
- Easily defeated by SIM swapping and protocol attacks
High-risk roles, finance, executives, admins, should use the strongest MFA available.
Monitoring and Detection: Your Early Warning System
Zero Trust isn’t just about access. It’s about real-time visibility.
Tools like Endpoint Detection and Response (EDR) and Security Information & Event Management (SIEM) help organizations:
- Detect suspicious activity
- Identify unauthorized access
- Catch attempts to upload data to personal platforms
- Isolate compromised devices
- Roll back ransomware activity
Monitoring is essential to Zero Trust, and especially to Zero Trust Security for Small Businesses, where early detection often determines whether an incident becomes a crisis.
Defense in Depth: Why Layers Matter
No tool stops every attack. Zero Trust relies on layered defenses such as:
- MFA
- Password managers
- Device hardening
- EDR + SIEM
- Network segmentation
- User training
- Incident response planning
- Disaster recovery
- Vendor risk assessments
Layered security reduces exposure and limits damage when incidents occur.
Reputation Matters Just as Much as Protection
Most cyberattacks are financially motivated, not personal, but reputation damage is still real.
Organizations that hide incidents often suffer worse outcomes than those that communicate transparently.
Being honest, following proper procedures, and responding quickly all help rebuild trust.
What SMBs Should Do Next
Zero Trust is complex, but implementing it doesn’t have to be overwhelming. The smartest first step is talking with a trusted security partner who can evaluate:
- Your risks
- Your workflows
- Your current tools
- Your business goals
Security isn’t one-size-fits-all.
A tailored roadmap makes all the difference.
If you’re ready to strengthen your cybersecurity posture, a conversation with ONE 2 ONE IT Solutions can help you understand where you stand and what your next steps should be.
Final Thoughts
Cybersecurity isn’t about fear. It’s about preparation.
Attackers only need one successful attempt.
You need layered defenses that hold up every day.
By applying Zero Trust principles like identity validation, MFA, monitoring, and least privilege, you can better protect your business, your clients, and your reputation.
Watch the full webinar replay above for the complete walkthrough.
